#
CI/CD (Continuous Integration and Continuous Deployment) for Docker based installations
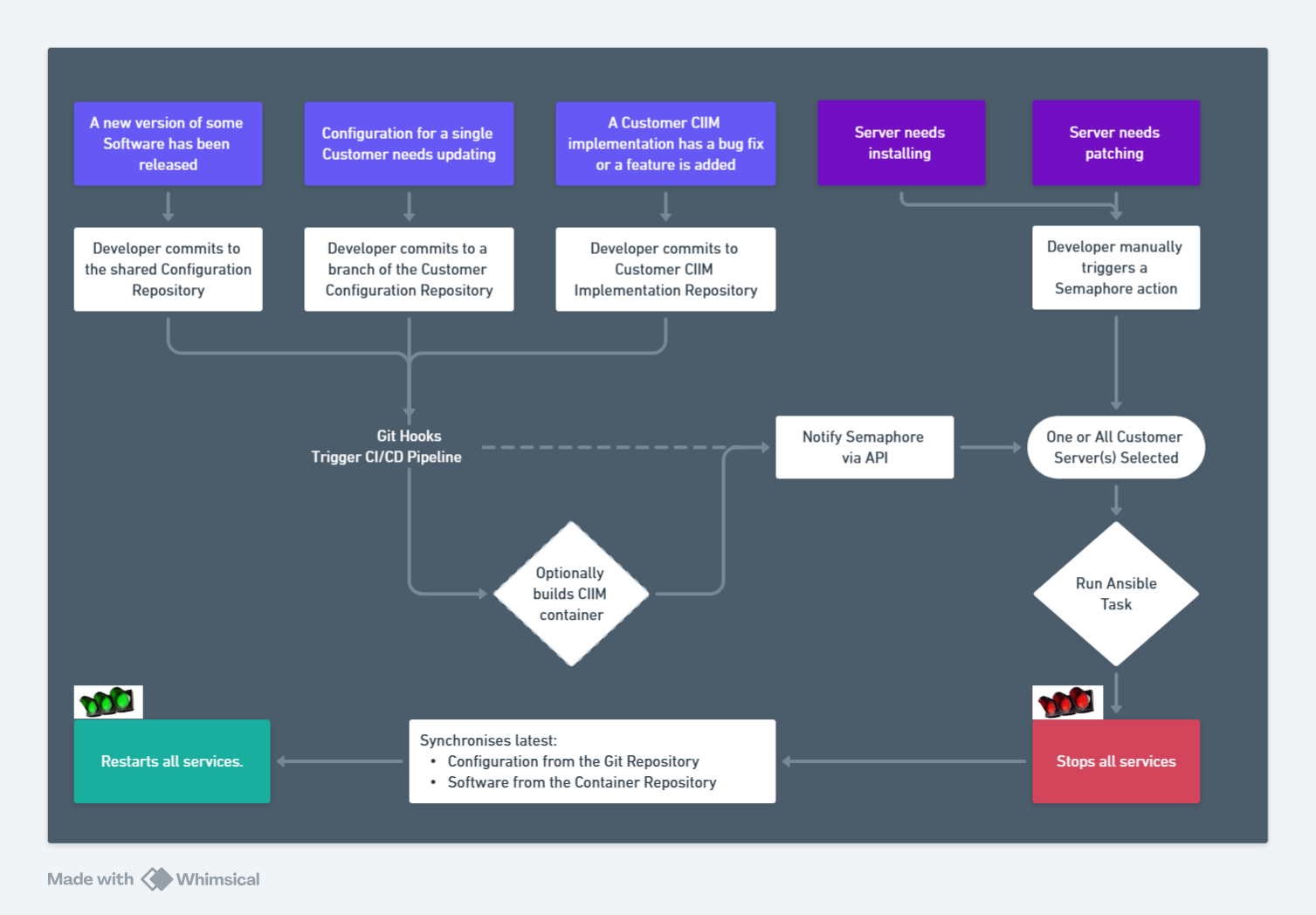
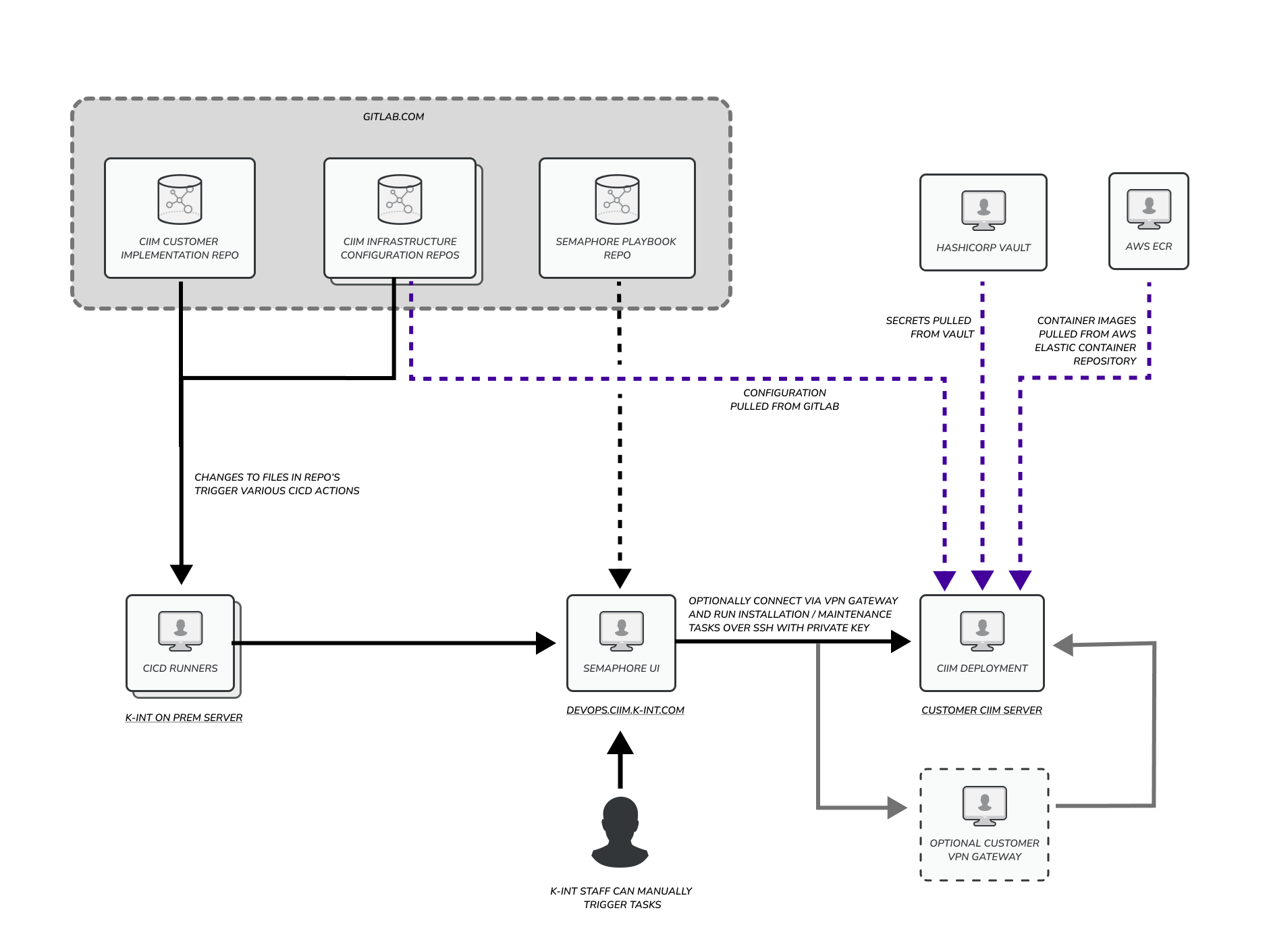
We use CI/CD to streamline and automate our software delivery process, helping us reduce manual errors and accelerate release cycles. By combining GitLab repositories, GitLab runners, and Semaphore, we’ve built a robust pipeline that provides fast feedback loops, allowing us to iterate more quickly and with greater confidence. This setup also enables us to maintain consistency across environments, respond rapidly to vulnerabilities to reduce deployment risks, and scale our development efforts more effectively.
#
Prerequisites
Our CI/CD process is designed to target Linux-based servers, with a particular focus on Ubuntu as the preferred operating system.
To ensure successful integration of your environment with our automated deployment pipeline, the following prerequisites must be in place:
VPN Access
If such exists, a VPN account should be provisioned for our DevOps automation tools to establish secure connections with your infrastructure. This may not be required if your server is not hosted behind your vpn.SSH Key Installation
Our DevOps public SSH key must be installed on all target server(s) intended for deployment access.Network Access Configuration
Firewall and network rules must allow inbound SSH connections fromdevops.ciim.k-int.comtypically on port 22. This host is deployed within AWS infrastructure and is accessible exclusively via the K-INT VPN.Ansible Integration
Semaphore, our deployment orchestration tool, utilizes Ansible playbooks to perform operations on target systems.
#
Semaphore
Semaphore is a web-based user interface and automation platform that provides streamlined execution of Ansible playbooks across infrastructure environments. We use it to ensure consistent installation processes, and automate routine server maintenance tasks such as patching, software updates, and health checks.
Optionally, Semaphore provides a built-in scheduling system similar to cron. Templates can be scheduled to run at defined intervals (e.g. weekly patching at 02:00 GMT every Sunday). This ensures consistent, unattended maintenance across environments.
Semaphore manages SSH authentication and secrets securely, they are stored in encrypted environments and injected at runtime. Templates can reference environment-specific credentials to isolate access.
Semaphore supports user roles and permissions, enabling granular access control for executing or modifying patching jobs. This ensures secure operation in teams or regulated environments. It also maintains an audit trail of all tasks executed.
#
Example supported workflows